Article by Rick Holland, Vice President, Strategy, Digital Shadows
Exploit kit activity is waning. Collectively these malware distribution tools used to be a prominent method of infection. They rely on compromised websites, malicious adverts and social engineering to direct web traffic to their landing pages and attempt the exploitation of vulnerable software. Operated by various actors and groups, exploit kits possess different features, use various exploits and distribute different malware to victims. Since June 2016 at least four of the major players in this area ceased to be active. In this blog, I wanted to explore which exploit kits are still around and propose some plausible scenarios for the future of the exploit kit landscape.
In memoriam
Before we look at the active kits, let’s take a moment to remember those that have gone on to greener pastures (at least for now, some kits have a habit of rising from the dead). Note I’ve only referenced the major players from the last two years in this section:
• In June of 2016 the Angler exploit kit disappeared. Angler’s disappearance was put down to the arrest of the Lurk group in Russia.
• In the same month, the Nuclear exploit kit disappeared; the reasons for this were unconfirmed.
• The Sundown exploit kit disappeared in April of 2017, following the leak of its source code online.
• Neutrino was reportedly inactive for at least two months as of 15 June, 2017, while one source claimed this was owing to its lack of profitability, this was not confirmed.
The survivors
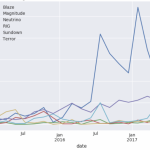
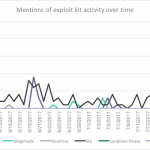
Despite these disappearances, the exploit kit landscape still represents a threat. Using mentions of exploit kits across social media and blogs that have been made by security researchers, we can formulate an indication of how active each exploit kit actually is. In the graph below, we can see that the RIG exploit kit has been mentioned most frequently from June until the time of writing; indicating it is likely to be the most prominent. All of the other kits shown in the graph, with the exception of Neutrino, still had some activity associated with them which showed they were still being deployed in the wild. Nevertheless, the rate at which they were detected and reported by researchers suggested they were likely less prevalent overall.
Researcher mentions of exploit kit detections on social media and blog sites could provide reasonable insight into levels of exploit kit activity. Considering the findings, we assess it is highly likely the threat posed by EKs is less overall to what it was in June 2016, and even the start of 2017. However, some exploit kits remain active and depending on the number of operators using them or the scale of the campaigns, the threat still remains. Exploit kits typically rely on out of date browsers, or browser plugins, therefore the primary mitigation for this threat is to ensure patches are implemented as soon as possible. In particular, exploit kit authors favour remote code execution exploits; our previous analysis of exploit kit payloads demonstrates this.
A potential reason for the decline of exploit kits
The reasons for these disappearances were unconfirmed in most cases, but at least one EK developer was reported to have claimed it was no longer profitable.
There were a number of other possible alternatives for this overall decline, including law enforcement action or the relatively resource intensive nature of exploit kit operations. Running these operations can be laborious:
1. Software development of the exploit kit
2. Acquisition of remote code execution exploits for browser-related software
3. Registration of large numbers of domains to host the exploit kits
4. Generation of traffic to the exploit kit landing pages for exploitation. Generating this traffic requires the compromise of websites, use of malicious advertising or use of spam emails
Furthermore, exploit kit operators contend with advert blockers, software updates and blacklists which all degrade the rates of successful exploitation. All of these factors suggest a realistic possibility that exploit kit developers or operators no longer consider them to be profitable. At a time when spam phishing campaigns were frequently used to distribute ransomware, a demonstrably lucrative type of malware, distributing malware via exploit kits is almost certainly highly resource intensive by comparison. We’ve recently seen actors experimenting with malware propagation within internal networks, shown by the TrickBot and Emotet banking trojans, which represents another method of spreading malware to multiple devices.
Are exploit kits dying out?
Based on the exploit kit trends we have observed over the last year, it is a realistic possibility that these tools will continue to be used less frequently as part of malware distribution in the long term. The use of large quantities of phishing emails containing document attachments with embedded scripts to download malware has been proven to be highly popular and successful in the least year. Therefore, threat actors could possibly move from exploit kits to malware distribution using this type of methods. However, there are multiple scenarios to consider:
1. Given a lack of competition one exploit kit might become the most dominant. Large amounts of business going to one kit could allow it to be developed more frequently and for its developers to acquire new exploits.
2. Following the disappearance of large exploit kits, new kits could emerge that attempt to fill the market gap.
3. Exploit kits could decline overall but still be used in more targeted attacks. The compromise of the Polish Financial Supervision Authority website in February 2017 involved the use of similar tactics, techniques and procedures to exploit kits.
4. Technology to detect and block malicious emails could improve to the point that this distribution method becomes less viable, resulting in a return to exploit kit activity which depends on end point management of software updates or other patch management solutions.
Scenarios are useful because they provide us with indicators to look for when examining threat landscapes. While it’s not always possible to say with full confidence how the future might look, the thought exercise itself can be useful. Despite these potential scenarios, exploit kits will almost certainly continue to remain a threat in the immediate future.