A report from Palo Alto Networks reveals the latest developments in cloud security trends.
The COVID-19 pandemic triggered the largest shift to remote work in history, and organizations struggled to migrate to the cloud and secure their employees working from home.
In the 1H 2021 edition of the biannual Unit 42 Cloud Threat Report, researchers from Palo Alto Networks analyzed data from hundreds of cloud accounts around the world between October 2019 and February 2021 to understand the global impact of COVID-19 on the security posture of organizations.
The report explains which types of threats increased the most, which industries were most heavily affected, how cloud security trends varied across different regions and what organizations should be doing to respond to the security threats they face in the COVID-19 era.
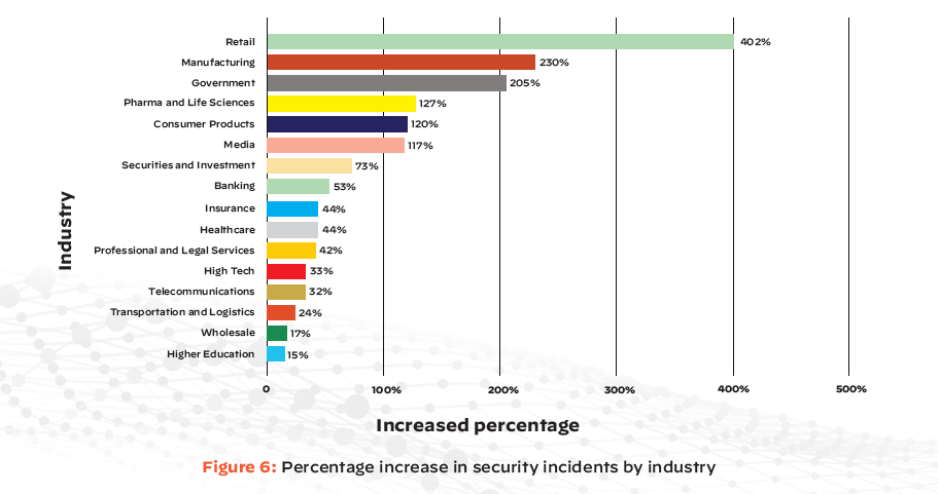
COVID-19 critical industries suffer spike in security incidents
Among the industries with the highest increases in security incidents were retail, manufacturing and government, which saw incidents rise 402%, 230% and 205%, respectively. Security incidents are defined as events that caused violations in security policies and put sensitive data at risk.
These same industries were among those facing the greatest pressures to adapt and scale in the face of the pandemic – retailers for basic necessities, and manufacturing and government for COVID-19 supplies and aid.
Cryptojacking in the cloud Is on the decline
From December 2020 through February 2021, only 17% of organizations with cloud infrastructure showed signs of cryptojacking activity, compared to 23% from July through September 2020. This is the first recorded drop since Unit 42 began tracking cryptojacking trends in 2018. This is likely because organizations are doing a better job of protecting against cryptojacking attacks.
However, research also shows that cryptomining activity fluctuated, increasing and then decreasing in intensity following key political and economic developments related to the pandemic. This suggests that incentives to mine cryptocurrency were impacted by the pandemic as well.
Sensitive data in the cloud remains publicly exposed
Unit 42 found that 30% of organizations host sensitive data in the cloud without proper security controls in place. Due in most cases to a simple lack of effective access-control restrictions, these businesses place personally identifiable information and other critical assets at risk. These risks could be contained by cloud security automation tools that audit for oversights such as improperly configured access controls.
Growing cloud security along with your cloud
As the report explains, implementing cloud security automation tools that can perform tasks – such as auditing Infrastructure as Code (IaC) templates for security risks, scanning cloud environments for misconfigured ports and comparing cloud configurations to industry-accepted security benchmarks – go a long way toward keeping cloud workloads secure, even as they grow in size. Hiring security engineers who understand cloud-native development and can help programmers build secure applications is important, too.
In short, as organizations scaled up their cloud environments in response to the pandemic, they did not always scale up their security and governance processes at the same rate. The result has been an explosion in cloud security incidents across a variety of regions and industries. Although certain risks, such as cryptojacking, are on the decline, it’s imperative that organizations take steps to plug the vulnerabilities that continue to lurk within their cloud environments.