Johannes Ullrich, Dean of Research at SANS Institute and founder of the Internet Storm Center, discusses the cyber-risk to routers and the trends his team has seen in the Middle East.
These days, any unprotected or inadequately protected device exposed to the Internet is at risk of attack from cybercriminals. This includes routers that businesses and individuals alike use to connect to high-speed internet connections, either via DSL or wireless (LTE). These are a popular and frequent target of attackers, since they are often easily attacked via exposed administrative control panels.
Once an attacker gets access to a device, the owner is less likely to notice the infection than on a desktop computer. Desktop computers usually have anti-virus installed to warn the user about malicious code and the performance impact of malware is more likely to be noticed.
An infected router can easily be used to intercept traffic from the network or to inject malicious content into traffic passing through the router. For example, an attacker can then wait until a user downloads an update and replace the update with malicious code.
Working in collaboration with DShield.org, SANS Internet Storm Center (SANS ISC) has been collecting reports from the routers of a large global network of volunteers since 2001 in order to analyse and provide early detection of specific attacks.
These volunteers operate sensors on their routers that detect unwanted traffic directed at these sensors. Ever since 2001, we have seen that a large percentage of these scans originate from compromised systems that are used by cybercriminals to find new victims.
Indeed, by analysing this data over the last few years, the SANS ISC has observed the rapid spread of botnets like Mirai and Satori. These botnets seek to connect to unprotected Internet of Things devices – like security cameras and digital video recorders that are exposed on the internet – and to then infect them.
They also attack unprotected routers. More recently, widespread attacks against D-Link routers made by MicroTik, among others, have been observed. These routers use vulnerable administrative interfaces which allow an attacker to execute commands, or modify configurations, without having to log in. Even if the router is patched, they often remain vulnerable if the administrator does not change default passwords.
The Internet Storm Center registered about 6,000 devices in Saudi Arabia that were emitting traffic consistent with such a compromise. It is likely that not all of these devices are affected. But, for example, over 300 of these devices have probed the Internet Storm Center’s sensors on port 23 alone over the last month. This indicates that Saudi Arabia and its neighbours are affected by these attacks just like any other country. The same vulnerabilities can also be exploited to gain access to corporate networks.
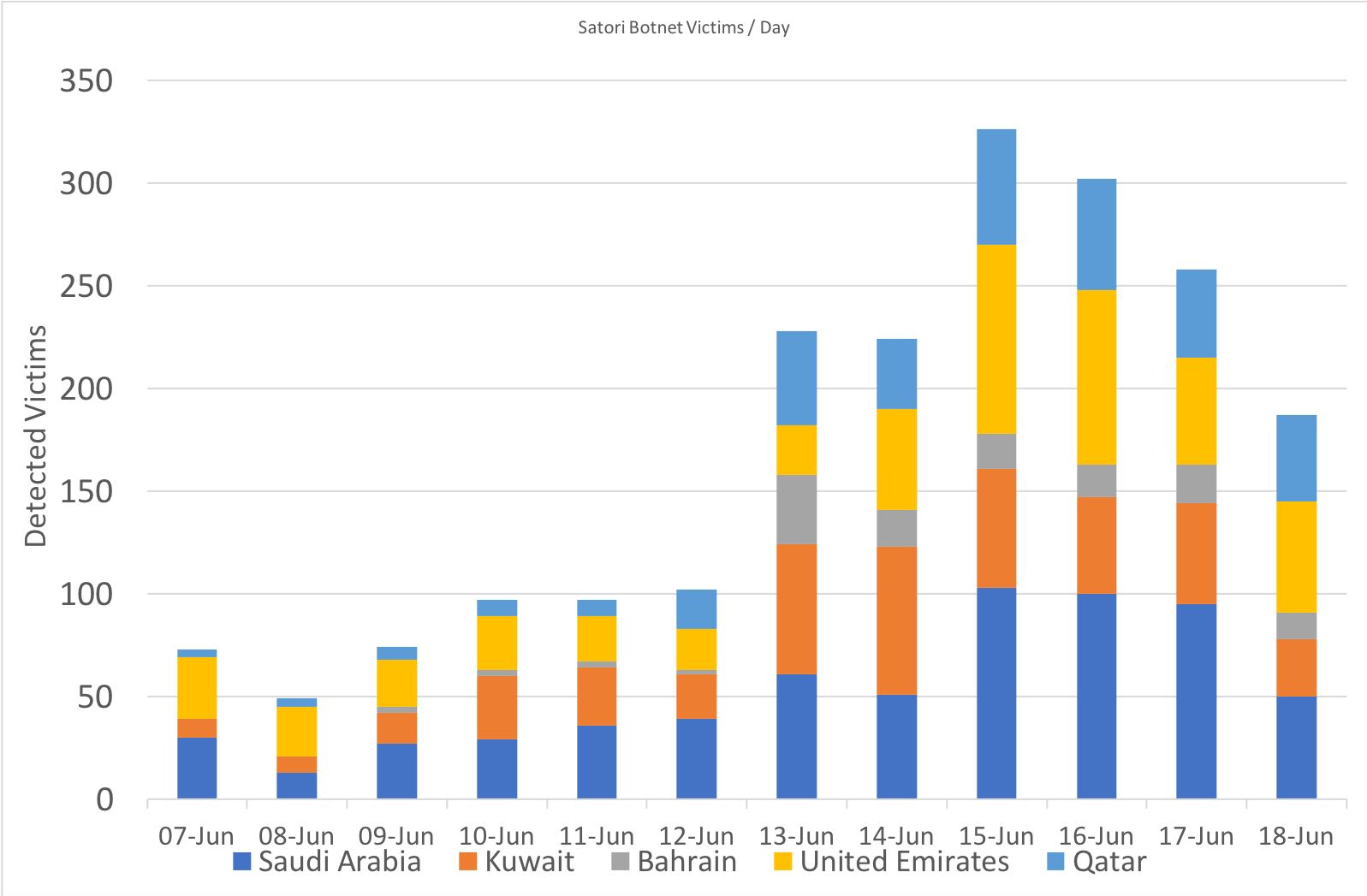
From June 15, one of the botnets, commonly named ‘Satori’, started to add a new exploit to its arsenal. This new exploit targets a vulnerability common in D-Link routers that exposes a web-based administrative interface on port 8000. The use of this new port can easily be used to identify affected devices worldwide, or in Saudi Arabia specifically. The graph [SEE BELOW] shows the rise of scans for port 80, 8000 and 8080 from Saudi Arabia and some of its neighbours over a period of 12 days.
Attacks against devices like this often go unnoticed but can have severe consequences. Cybercriminals can use the access they have gained to these devices to then intercept traffic passing through it. More recently, a botnet known as VPNFilter was discovered with a more sinister mission.
Unlike most similar botnets, VPNFilter cannot be simply removed from the device with a reboot. Instead, the bot alters the device’s firmware and will try to re-infect the device after a reboot. VPNFilter includes various modules that can be used to sniff traffic passing through the device, or that can use the device as a platform to launch attacks against other networks. VPNFilter is believed to have been targeting energy companies in the Ukraine.
Most malware infecting devices, however, have a much more benign goal – mining cryptocurrencies. Cryptocurrencies are currently by far the most common method that criminals use to monetise attacks from the devices they are taking over. No device is too small. Monero, for example, one of the primary cryptocurrencies being targeted by criminals these days, can be mined very efficiently on smaller devices and PCs.
A typical attack will first scan the device for common vulnerabilities or well-known default passwords. If the attack is able to access the device, then it will often remove competing malicious code and install its own ‘miner’ software. The software will then try to use as much of the device’s CPU as possible in order to mine cryptocoins. The attacker will usually have no regard whatsoever for any collateral damage caused to the user or the device.
Affected firewalls often become unresponsive and in some cases may overheat and break permanently. In fact, in multiple experiments run by the SANS ISC, it only took a few minutes for a vulnerable device to be attacked and taken over once it was connected to the Internet. These attacks affect any Internet connected device.
The speed at which vulnerable devices are infected shows how important it is to protect yourself from these attacks. As even home users are affected, it is important to implement some simple and effective guidelines. First of all, always change the password that comes with your device.
Default passwords are the most common attack vector. Unfortunately, in some cases it may not be possible to change the password. This is particularly true for passwords that are installed by manufacturers as a backup or support account. The user often doesn’t know about these accounts or is unable to change the passwords.
For this reason, all remote access methods should be disabled or severely restricted. Manufacturers will also often release updates if a new vulnerability becomes known. It can be tricky to apply these updates to some devices, but it is important that you do so, since at SANS, we have seen in the D-Link case how a new vulnerability is being exploited within a couple of days.