Ransomware remains a key challenge for organisations but CISOs do have some weapons in their arsenal. Zero Trust is one approach which has risen in popularity in recent times. Sally Adam, Marketing Director at Sophos, talks us through the findings of recent research highlighting a correlation between the adoption of a Zero Trust approach and experience of a ransomware incident, as well as the role of Zero Trust Network Access in preventing such attacks.
Organisations with recent direct experience of a ransomware attack have considerably higher adoption of Zero Trust network access (ZTNA) technology than those that haven’t fallen victim.
A study of 5,400 IT professionals has revealed a correlation between direct experience of ransomware and adoption of a Zero Trust approach.
Organisations that had experienced a ransomware attack in the previous year (defined as multiple devices being impacted but not necessarily encrypted) reported considerably higher levels of awareness of the Zero Trust approach and were more advanced in their implementation of Zero Trust network access (ZTNA) solutions than those that hadn’t experienced an incident.
It is likely that these organisations’ direct experience of ransomware accelerated the implementation of a Zero Trust approach to help prevent future attacks.
The findings result from an independent survey of 5,400 IT professionals in organisations with between 100 and 5,000 employees that was conducted by research house Vanson Bourne on behalf of Sophos in 2021.
The role of ZTNA in preventing ransomware attacks
Breaching the victim’s network is one of the first steps in a ransomware attack. The rapid increase in remote working over the last two years has hugely increased the opportunity for attackers to exploit vulnerable VPN clients to get a foothold in an organisation. Once inside, they are often free move laterally throughout the network, escalating privileges and progressing the attack.
By eliminating vulnerable VPN client software, granularly controlling access based on device health and identity, and micro-segmenting applications, ZTNA stops attackers from both breaching the organisation and from moving around it, even if they obtain legitimate credentials.
[To learn more about the role of lateral movement in ransomware attacks, read the Sophos research report Windows Services Lay the Groundwork for a Midas Ransomware Attack that details how adversaries exploited remote services and access tools to hold a technology company to ransom.]
Finding one: Ransomware victims have much greater familiarity with the ZTNA approach
IT professionals in organisations that had been hit by ransomware in the previous year are almost 50% more likely be ‘very familiar’ with the ZTNA approach than those whose organisations hadn’t experienced an incident (59% vs 39%). This rises to 71% among those whose organisations had been hit and they paid the ransom.
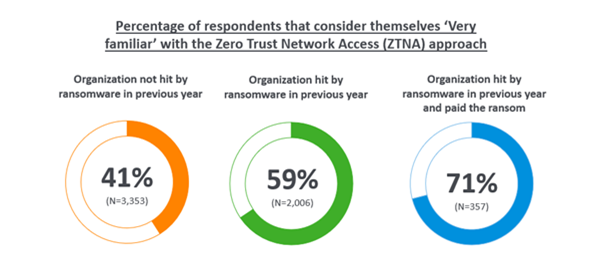
Further illustrating this point, just 10% of ransomware victims have little or no familiarity with ZTNA, compared with 21% of those whose organisation hasn’t fallen victim.
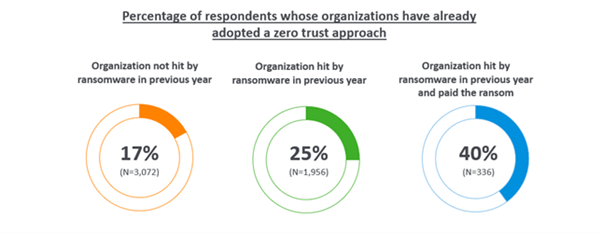
Finding two: Ransomware victims are more advanced in their adoption of the Zero Trust approach
One quarter (25%) of those whose organisation experienced a ransomware attack in the previous year have already fully adopted a Zero Trust approach, rising to 40% of those whose organisations were hit and paid the ransom. In comparison, just one sixth (17%) of those that hadn’t experienced an attack have already fully migrated to this approach.
Finding three: Ransomware victims have different motivations for adopting a Zero Trust approach
Respondents were asked about their motivations for adopting a Zero Trust approach and, while there were several commonalities, there were also clear areas of difference.
‘To improve our overall cybersecurity posture’ was the most common motivator among both victims and non-victims
The second most common motivator among ransomware victims was the desire to ‘simplify our cybersecurity operations’ (43%), potentially reflecting that complex security had contributed to their previous attack
Ransomware victims are also heavily motivated by ‘supporting our move to increased use of the cloud’ (42%). This dropped to 30% amongst those that hadn’t experienced a recent attack
Similarly, ransomware victims were also much more likely to say that ‘to move from a CAPEX to an OPEX model´ was one of the main factors behind their Zero Trust approach adoption (27% vs. 16%, and rising to 34% among those that had been hit by ransomware and paid the ransom)
Finding four: The pandemic was more likely to positively impact the Zero Trust adoption plans of ransomware victims
For many organisations the pandemic had a positive impact on their plans for adopting a Zero Trust approach. For many, it created a need for Zero Trust that they didn’t have before. This is understandable: many companies and public bodies were previously wholly office-based and so didn’t have a need to provide secure remote access.
Half (50%) of ransomware victims and 36% of non-victims reported that the pandemic enabled them to move budget to adopting a Zero Trust approach, while many also reported that it enabled them to divert people and/or money from other activities to the move to Zero Trust.
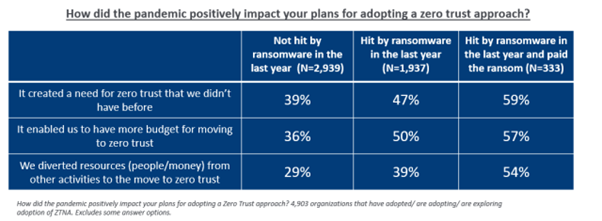
The survey findings highlight that organisations that fell victim to ransomware and paid the ransom were most likely to experience a positive pandemic impact on their Zero Trust adoption. It seems that pain of the ransomware attack might have concentrated minds and resources on effectively mitigating a future incident.
Introducing Sophos Zero Trust Network Access (ZTNA)
Sophos ZTNA is a much more secure and easy-to-manage remote access solution that delivers a transparent, frictionless experience for end-users.
- By removing the need for VPN clients, Sophos ZTNA reduces the attack surface, making it harder for ransomware actors to get on your network
- Sophos ZTNA constantly checks user and device security, delivering continuous high-level of controls and preventing attackers from exploiting a previously authenticated user’s access
- Granular access controls enable you to easily restrict access to specific resources to those who need them, preventing adversaries from moving laterally across your network
- Sophos ZTNA uses the same agent as Sophos Intercept X endpoint protection, enabling customers to enhance their protection without adding device overhead
- It is managed from the cloud-based Sophos Central platform, enabling customers to manage all their Sophos solutions via a single interface for enhanced day-to-day management and control
With the average cost of ransomware remediation now US$1.85 million for small and mid-sized organisations, moving to secure remote access via Sophos ZTNA is a sensible investment.


