Barracuda Networks, provider of cloud-first security solutions, published its Fifth Annual Threat Spotlight on Ransomware. The new report looks at ransomware attack patterns that occurred between August 2022 and July 2023.
Barracuda researchers analysed 175 publicly reported successful ransomware attacks across the world between August 2022 and July 2023, and in the primary categories Barracuda has been tracking, municipalities, healthcare and education, the number of reported attacks have all doubled since last year and more than quadrupled since 2021. Researchers also saw a spike in the number of attacks on infrastructure-related industries.
While successful ransomware attacks targeting infrastructure-related industries are lower in volume compared to the top three sectors, these industries also experienced more than twice the number of attacks compared to last year. The analysis revealed similar patterns of escalation in other industries, particularly ransomware attacks on software businesses.
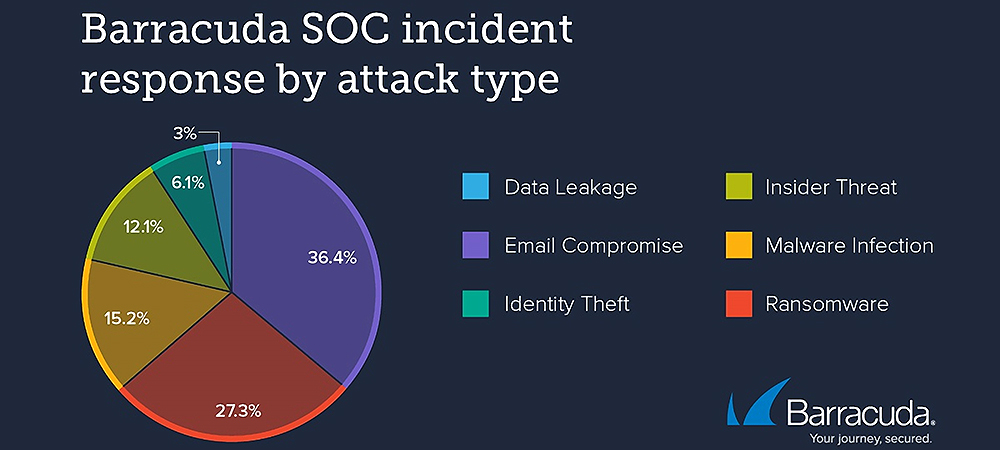
In the past 12 months, Barracuda’s SOC-as-a-service team observed the following types of incidents: business email compromise, ransomware, malware infection, insider threat, identity theft, and data leakage. Ransomware accounted for 27.3% of incidents, second only to BEC, 36.4%.
This year, Barracuda researchers also took a closer look the impact of generative AI tactics on ransomware attacks, looking at ways cybercriminals can use these capabilities to strike faster and with better accuracy.
The number of successful ransomware attacks continues to climb and shows no signs of slowing down. Recent advances in generative AI will only help ransomware gangs increase the rate of attack with more effective cyber weapons. That is why it is essential for organisations to have tools in place to detect and prevent attacks, but also to be resilient and prepared to recover from an attack.
Another important development in the past year is the rise of generative AI, which you can bet attackers are using to create well-crafted phishing emails. Using generative AI’s writing capabilities, cyberattackers, including those looking to launch ransomware, can now strike faster with better accuracy, as the spelling errors and grammar issues in phishing emails are more easily eliminated, making attacks more evasive and convincing.
For years, everyone has been trained to spot email attacks by looking for bad grammar and spelling mistakes, a deficiency that is likely non-existent today given what attackers can create using generative pretrained language models, and in some cases, in different spoken languages, even using automated scans of social media to make attacks more customised.
Security researchers are already showing how attackers can use the code-generation capabilities of generative AI to write malicious code for exploiting software vulnerabilities. With these changes, the skill required to start a ransomware attack could be reduced to constructing a malicious AI prompt and having access to ransomware-as-a-service tools, leading to a whole new wave of attacks.
Researchers are also seeing many incidents where under-resourced organisations seem to fall victim to ransomware multiple times because their business continuity and disaster recovery plans are far behind. We have seen attackers going after backup systems especially if they are hosted in the same domain and run as virtual systems.
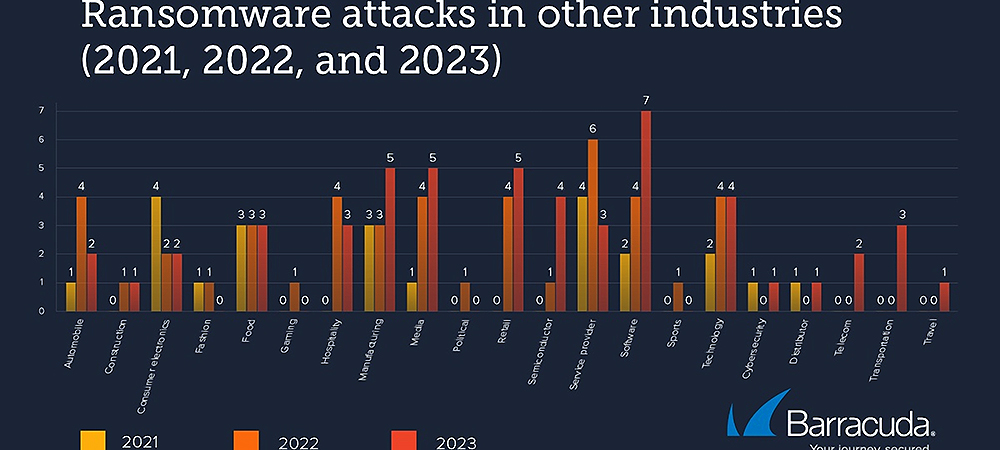
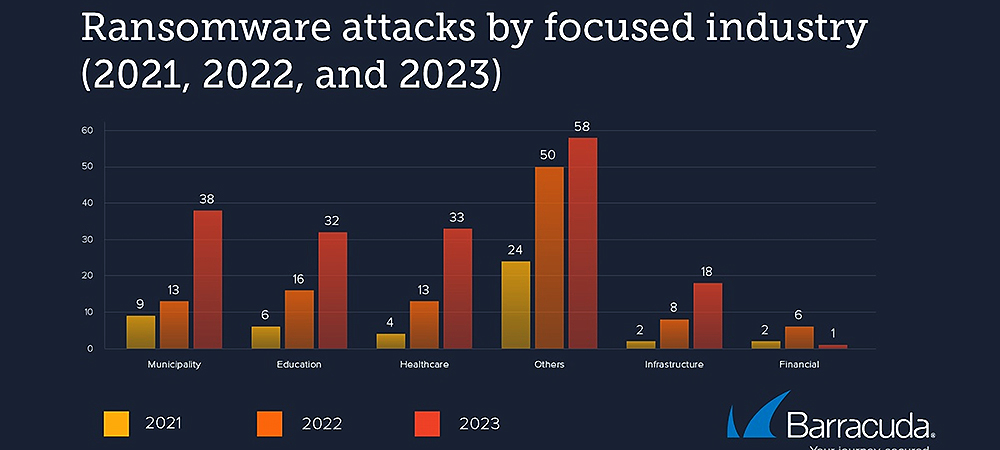
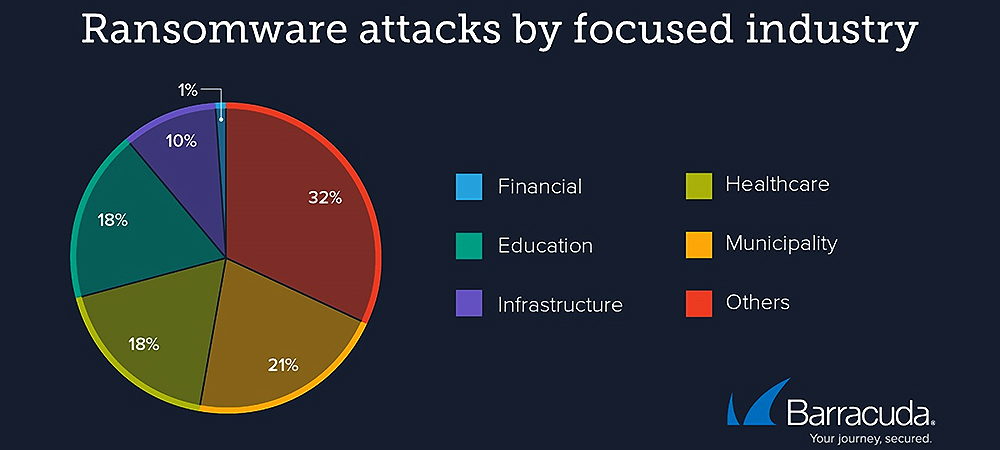
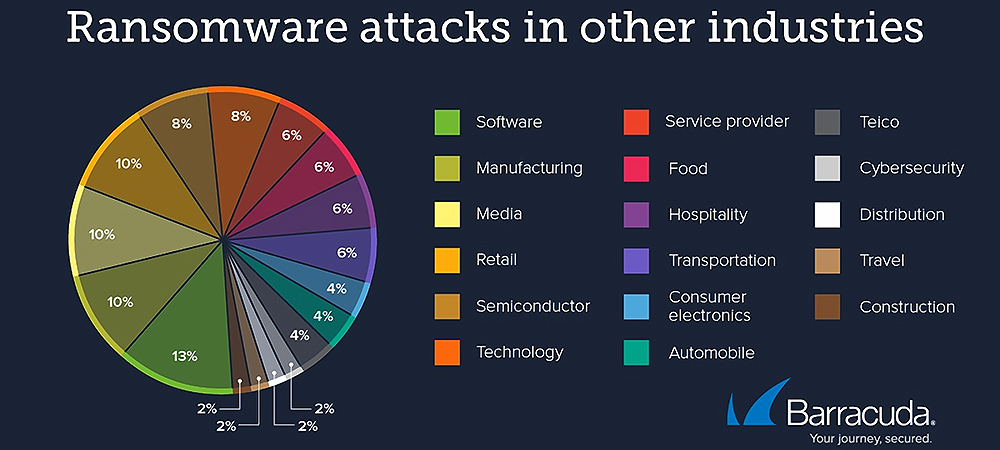
Source: Fifth Annual Threat Spotlight on Ransomware, Barracuda Networks